MOBILE edit
Compelson MOBILedit Forensic Express is a versatile application that acts as a data extractor for mobile phones and cloud accounts. In addition, it acts as a data analyzer and report generator. This powerful 64-bit application applies both physical and logical analysis methods extremely efficiently. With the integrated application analyzer, the GPU-assisted password and PIN breaker as well as the function for recovering deleted data, MOBILEdit offers all the necessary tools to evaluate mobile phones immediately and easily.
In addition, the software allows analyzing ADB (Android Data Bridge) backups and iTunes backups. It supports a wide range of mobile phones, from older models to current devices. Support is continuously updated and expanded through live updates. With granularly adjustable reports and an intuitive user interface, MOBILEdit is a true multifunctional tool. In addition, multithreading enables the simultaneous analysis of several devices.
Comparison
Compared to other products, Compelson Mobile Edit is extremely cost-effective. Due to its data compatibility with industry standards, it can also be used as a supplement to existing Mobile Analysis packages. Request a non-binding offer today. Also note the possibility of integrating Camera Ballistics for the origin analysis of photos.
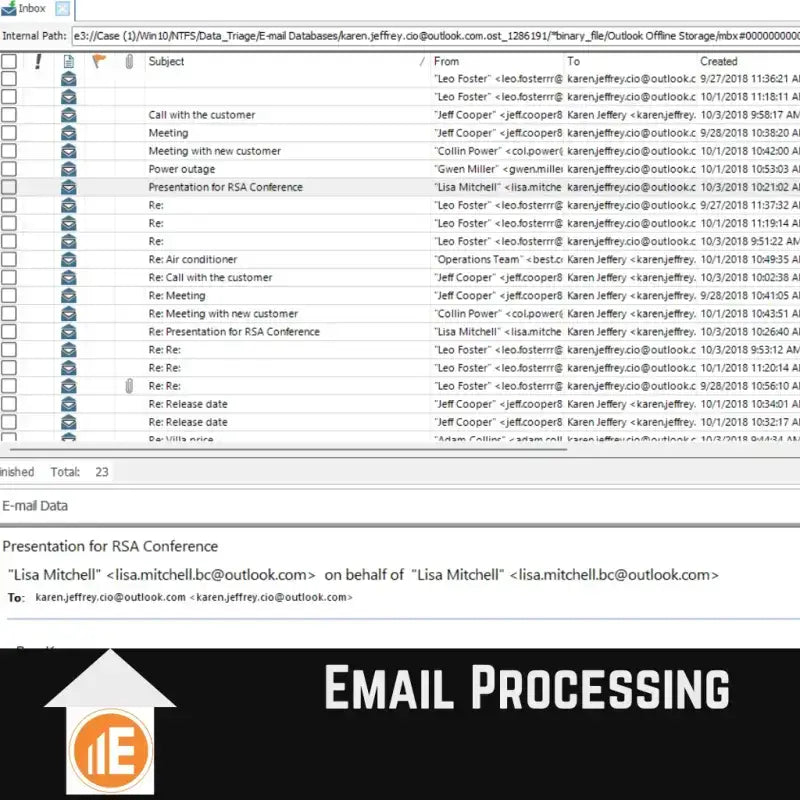
Investigators are faced with a variety of data types when analyzing forensic data. Find out here which data can be extracted, analyzed and presented. However, the amount of data extracted depends on the phone model, its operating system and its condition.
Key Features
Forensic data extraction for most mobile phones.
Fast password cracking thanks to GPU (Graphics Processing Unit) acceleration and efficient multi-threading.
Examination of iTunes backups.
Examination of Android ADB backups.
Determination of app data.
Photo/image recognition function.
Recovery of deleted data.
Compatibility with Cellebrite UFED Data Analyzer.
Compatibility with Cellebrite UFED Data Generator.
Compatibility with Oxygen Data Analyzer.
Report generator for detailed reports.
Ability to unlock cell phones.
Integration with Camera Ballistics possible (for checking camera recordings as evidence).
Unbeaten in the NIST test
The National Institute of Standards and Technology (NIST) has developed a methodology to test mobile forensic tools and measure the reliability of products available on the market. In this test, Compelson Mobile Edit scored outstanding and proved to be an extremely reliable and powerful tool for forensic data analysis of mobile devices.
Reports & Exports
MOBILedit offers different options for forensic reports and exports:
HTML: Creates a hierarchical structure that allows the data to be easily browsed with any browser.
PDF: The data can be exported as a single file or in multiple separate files in Acrobat Reader format.
XML: The data can be opened in Excel.
XLS: Exports the data as an Excel workbook.
UFDR: The ability to export the data as a Cellebrite Report file.
MOBILedit exports the processed file structure from the phone.
MOBILedit secures the backup of the RAW files from the phone.
Export and backup can be compressed and encrypted using AES encryption with MD5 or SHA256 hashes.
contact report
The contact report is a valuable tool in uncovering the suspect's connections. It contains comprehensive contact data that has been carefully extracted and analyzed, including deleted contacts where available. The data for the contact analysis comes from various sources such as the phone book, internal memory, vCard files, SIM cards, cloud accounts and applications. The report allows the investigator to search specifically for names, numbers, deleted contacts or other information. The report also provides detailed information about when the contact was created, when it was last modified, and what type of account it is (e.g. WhatsApp, Cloud, Gmail, Facebook, etc.). Here the investigator will find important information such as phone numbers, email addresses, home addresses, birthdays, employers and contact profile pictures that will help put a face to a name.
Through a contact analysis, the investigator can find out which contacts the suspect had close contact with and discover important connections. The contact analysis lists the number of messages and calls sent and received, including the talk time in minutes, and ranks the contacts in descending order of the number of communication events with the suspect.
The contact report allows the investigator to identify all phone, email, cloud and application accounts associated with the suspect's device. This information is extremely valuable in solving the case.
News:
The Messages report retrieves and displays all messages in full, including deleted messages if available. This includes standard phone messages such as SMS, MMS, iMessages, email messages, SIM messages, and application messages. The report can be customized to suit your needs and sorted by contacts, timeline, conversation view, or both.
Communication history:
The report allows for an efficient review of the complete conversation histories. The conversations are separated by contacts and sorted in time order. All SMS, MMS, iMessage and application messages, including encrypted messaging apps, are included in the reports.
Call list:
The call history contains details of all phone calls made through mobile services and applications, including deleted calls. The report shows the date and time of the calls, call duration, the source of the call (e.g. mobile phone, Facebook, WhatsApp, etc.) and the associated contact and phone number.
E-mail:
The Email report retrieves and displays emails in full, including deleted messages where available. The report can be customized to your needs and sorted by contacts, timeline, or conversation view.
Advanced application analysis:
All installed applications are listed and analyzed in detail, including deleted application data, if available. The Application Report provides a comprehensive overview of the applications on the device. It is possible to limit the search to specific applications or perform an analysis for all applications in the device. Particularly relevant is the ability to read encrypted messages in various applications. The RAW application data is saved in the export folder, which allows for additional processing and analysis. MOBILedit supports hundreds of applications, and the list is constantly growing.
MobilEdit is designed to integrate seamlessly with other forensic tools in your lab. It allows you to import and analyze data files exported from Cellebrite UFED and Oxygen reports, which can help uncover potentially missed data. Additionally, you can export any data extracted using MOBILedit Forensic Express to UFED, which allows you to use the UFED Viewer or Analytics for further processing and to advance your investigation.
Deleted data:
Deleted data is often crucial in an investigation. Our software presents details of deleted data in a special, comprehensive deleted data report. Deleted data is also shown in each individual analysis report. Whether it is deleted calls, SMS, MMS, calendar entries, notes, application data or other evidence, MOBILedit Forensic Express intensively searches databases for caches and hidden files to find the largest possible amount of deleted data.
Passwords:
The password report displays passwords from various types of accounts and applications. On iOS devices, all system passwords and most application passwords are managed through a dedicated and encrypted keychain. Our software can decrypt the keychain and retrieve all passwords stored in it. This includes Wi-Fi passwords, Apple ID passwords, passwords stored in Safari, as well as various email and application passwords and passwords stored in web browsers and other accounts. From Android devices, Wi-Fi passwords are retrieved.
WLAN networks:
The Wi-Fi network report displays detailed information about all Wi-Fi networks stored on the device. The report shows the history of Wi-Fi connections in chronological order. This includes the Wi-Fi network name, last connection time and date, auto-connection time and date (shows whether the suspect has repeatedly visited the network location), SSID, BSSID, and security mode. In addition, continued logs and connection times can also be supported. Wi-Fi network passwords are also recovered and displayed in the password report.
Pictures:
The Image report lists images from the phone's file system, including those retrieved from apps. Potential images stored in temporary files or caches are also detected. The option to view large images at full size allows one image per page to be shown in an additional section of the report. Duplicate images, such as emojis, can be filtered to keep reports uncluttered.
Photos:
The photo report retrieves all the phone's device and application photos, usually from the DCIM folder. Deleted photos sent via MMS or from an app can also be recovered if the storage allows it. The Apple HEIF image format is also supported.
Radio cells:
Data from cell towers to which the phone in question was connected can be retrieved. Received cell locations are displayed individually on the map via a link.
Audio:
Audio files from the phone and apps are copied. The audio report allows you to play an audio file by simply clicking on it. The report also includes the file path, creation and modification time, length of the audio file and its size.
Video:
Video files from the mobile phone and apps are copied. The video file report allows you to play a file by clicking on it. It also shows the file path, creation date, modification date, encoding, length of the video, size, frame rate, height and width.
Calendar:
The calendar and organizer are searched and analyzed. The data is prepared in four different reports. It is possible to customize the search for calendar entries, notes and tasks within a certain period of time or to perform a complete search.
The Calendar report shows the different device and application accounts where events were created and saved. Details include the account source, name, account owner, email address, and the number of events associated with the calendar.
The event report lists all events from the device and apps in detail, including deleted entries from calendars and other sources where events were created. The details include the calendar where the event was created, summary, description, start time, creation time, modification time, end time, and recurrence. The events can be displayed in ascending or descending order.
Tasks are detailed in the task report, including the full text, creation time, modification time, start and end time, and information about whether the task was deleted.
Notes, including deleted or removed notes, are summarized in detail in the Notes Report. The report includes the note title, summary, full-text content, and the times of creation, modification, and deletion.
Documents:
All common document formats can be read and presented.
System logs:
A report of system logs and DumpSys files from Android phones. Android stores these files for debugging and monitoring. They contain system data such as current locations, recently connected Wi-Fi networks, running apps, recently launched apps, current cell locations and signal information, current Bluetooth MAC address and name. These files are listed in the System Logs section in the HTML and PDF reports and can be opened simply by clicking on their file names. Their contents are analyzed and displayed in various reports for Wi-Fi networks, GPS locations, notifications, etc.
File system:
The file system report contains three sections:
Internal – contains the unformatted file system.
Application File System – contains data files from apps.
Extra File System – These files are not physically present on the device, but come from the iTunes backup. On Android, these are Content Providers, System Logs and DumpSys files.
Timeline:
The timeline provides a detailed insight into all device activities. The report summarizes all extracted items with a time stamp and displays them chronologically. The parameters of a timeline can be customized. For example, you can specify that only a timeline with calls and messages is created.
Photo recognition:
This feature automatically finds suspicious content in photos such as weapons, drugs, nude photos, currency, and documents. Photo recognition uses AI and learns on its own. You can analyze unlimited photos and save time by avoiding manual searches. Photos are automatically categorized so investigators can clearly archive cases and present the suspicious content in a detailed report.
Bookmark:
The Bookmarks report collects all browser bookmarks from iOS phones (Safari) and on Android devices up to Android 5.1. In later versions of Android, only bookmarks can be retrieved on an app basis. The report can be sorted by time or name (alphabetically).
Bluetooth Pairing:
The Bluetooth pairing report is available for both Android and Apple iPhones. In this report you will find the name of the Bluetooth connection, the address of the paired device, the status. On iOS you will also find the date and time of the connection.
Contact analysis:
Contact analysis provides the relationships between contacts in different communication types. Contacts who are rarely contacted can be skipped.
Notifications:
Notifications about the device and applications are shown in detail and can be retrieved from iOS and Android devices. The report shows all content, including source and timestamp. On iOS, notifications that are no longer active and contain information that is no longer available are also included, such as emails and messages from apps that do not store them in databases. On Android, only active notifications can be retrieved.
Browser history:
The Browsing History report contains the history of all browser applications. Each entry consists of the URL visited and the time of access. In some cases, the total number of visits to the URL is also available with the timestamps of each visit. The report can be customized in alphabetical order or by time order.
Internet search:
The Internet search history report contains queries from the web browser with timestamps. System-wide web searches are only available on Android 5.1 and earlier devices. Web search data is also collected from browser application analytics.
Geo-IP data:
The GPS Location Report contains comprehensive information about the possible GPS location data of the device and apps. This includes last known locations that can be read from Android. The analysis and report provide valuable insights from mapping, fitness and transportation apps such as Google Maps, Pokémon Go, Nike + Running, Uber and many others. Some applications can even capture GPS data about the entire route and display it with their recorded and stored timestamps. Photos and videos can also contain GPS locations in their metadata. It is possible to customize the location search and report by time or to search for locations near specific GPS coordinates.
Unlocking mobile phones can allow access to the physical data of the device on many Android phones, even if it is protected by a password or gesture. Likewise, it is possible to bypass the lock screen on many phone models.